Malware takes a leap forward
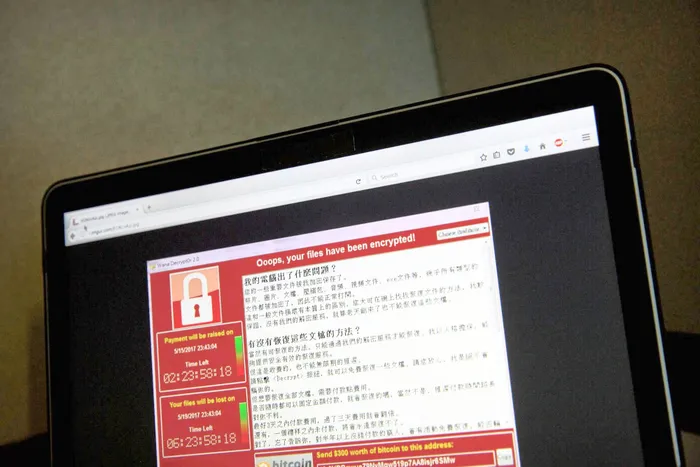
DANGER: A screenshot of the warning message from a purported ransomware attack in Taiwan on Saturday. Picture: AP DANGER: A screenshot of the warning message from a purported ransomware attack in Taiwan on Saturday. Picture: AP
The WCrypt ransomware has affected an estimated 200 000 computers across the world and continues to do so. It has so far made around 26.11 bitcoins, approximately R600 000, for the criminals behind it.
Of course, these figures are bound to increase over the next three to six days.
There are many interesting features in this WCrypt ransomware that are relatively novel or never seen before. For starters, you don’t need to do anything stupid to get infected. You don’t need to click on a suspicious link or open an email attachment to get your files encrypted and held to ransom.
It uses a vulnerability, with a patch available since March 14, that allows Windows machines to infect and get infected via SMB, the protocol used to share folders and files, print, and so on.
It also has other worm-like features that allows it to attack not only local computers but those situated in other networks or countries.
WCrypt is unique in multiple ways. For example, in the past, we were used to ransomware campaigns being launched against a given company, or sector, or even country.
This had many advantages for cyber criminals: typically, only one law enforcement agency would be called, they will keep a low profile, the resources devoted to the investigation and attribution will be limited, and the chances of ransom paid quite high, as institutions could sometimes get out without reputation damage.
WCrypt has gone nuclear in this respect, attracting the unwanted attention of many law enforcement agencies and industry and making them collaborate and co-ordinate in previously unseen fashion.
It is early days yet, but it seems that the cyber criminals made some suboptimal design and coding choices. First, the amount of ransom that they request is probably too small.
Also, the by now famous “kill switch” that has helped to slow down the spread of the malware is most probably a primitive self-defence technique. It seems the authors did not realise this feature could be used to stop the malware from infecting more systems.
Of course, this is only temporary good news as it is very easy for the criminals to correct this weaknesses and launch a new campaign without the kill switch.
Apart from the authors, other cyber criminals can take the malware code and create copycats without this feature, to continue targeting more systems across the world.
There is an important lesson to be extracted from all this. The National Health System is critical for the UK’s well-
being and as such it should be protected adequately because otherwise these attacks will cost lives. Attacks will only get worse in the future, so we need proper IT resources, much better security and a back-up policy that will guarantee that when the worst happens, trusts will be able to get back on track soon afterwards to continue saving our lives and those of our families and neighbours.
Many institutions, and unfortunately many critical institutions and infrastructures such as hospitals, firefighters, the police, and so on don’t have enough resources to devote to cyber security. The government should ensure this is done in a sensible and orderly manner.
It will happen again and it will be worse. The binaries of the ransomware are there for all to study, modify and use. Creating it is not technically challenging.
There will be copycats with similar capabilities and slightly different features.
That is why it is so important to patch your Windows systems, disable SMB and implement a proper back-up solution that will guarantee recovery in case of catastrophic damage in hours - not weeks or months.